Recommended reading is Link Aggregation/Trunks and VRF.
Overview
vPC is a technology that allows two devices on separate links to show up as one virtual device to access layer devices. This is NOT switch stacking; devices stay as separate management planes.
The device connected only sees it as a link aggregation and does not need any special setup. It can be a switch, server etc.
Concepts
Keepalive Link
The keepalive link is used to send hello/heartbeat messages between peers. It is used as a detection method to determine if a peer goes down as well as negotiating primary and secondary.
The link also has the job of telling the system if the peer is down or just the link. If the peer-link (datalink) goes down but not the keepalive link the other peer is most likely still up. If the keepalive and the peer-link go down, then the peer is most likely not active.
There are two options to set this up. The first and best option is to create a VRF with layer 3 interfaces terminated to it on each switch. This will give a separate routing table for just this link. The second option is to use the mgmt. ports of each switch.
Do not run the keepalive on a SVI that is running on the peer-link. This defeats the purpose.
We will use the first option.
Peer-link
The peer-link is used to actually pass data between the peers. It is essentially an aggregated link between the switches that has a vPC peer-link identifier. This is recommended to be aggregated links of at least 10Gb/s. If on a chassis switch they recommend them to be on separate line cards.
This link also passes CFS (Cisco Fabric Services) traffic, and it is recommended to statically set the spanning-tree port type to network (no idea what the fuck this means either, white papers were not clear).
Member link
The member link is the virtual link that will run to whatever access device you are using. This is a standard trunk and does not need special configurations other than being put into vpc.
vPC Domain
The vPC domain is an ID range of 1-1000 that ids/separates vPC instances. As such this needs to match between peers.
Topology
The following diagram in CML shows a basic vPC setup.
The two nexus devices are connected by a peer-link and a keep-alive link.
- Peer-link is used to send data such as network/vlan traffic, and BPDUs (e1/1-2) and are technically normal trunks/aggregated links.
- Keepalive link is used for dedicated vPC heartbeat communication (e1/3) and is put into its own VRF.
- Interfaces e1/4+ are used as normal trunks/aggregated links. As stated above they show up as one device.
- HSRP is enabled for vlan 10, 11, 16, and 20.
Configuration
We will go ahead and enable the features that we will be using now. The following setup will use vPC to an access layer switch.
VPC and LACP will be used for this, we will not be using FabricPath. You do not need to use LACP, using mode ON instead will work. Cisco recommends LACP. Because of course they do.
(config)#feature vpc
(config)#feature lacp
(config)#feature hsrp
(config)#feature interface-vlan
As stated, we will be creating a VRF for the vPC keepalive link.
If you are unfamiliar with VRFs I recommend looking at the VRF page just so you understand the concept of what a VRF is. This will be a basic VRF-Lite setup, and we will not be using advanced features. We will be using the context configuration, however.
Configurations will be for both of the nexus switches with some changes needed to be made to things like IPs. The access device we will configure last and will be labeled as such.
We need to create a VRF for the vPC keepalive link.
(config)#vrf "context" "VPC_KEEPALIVE"
We will now add the interfaces to the VRF. You can use a /30 or a /31 for this link, configure the IP after setting it to a VRF member.
(config)#int "e1/3"
(config-if)#no switchport
(config-if)#vrf member "VPC_KEEPALIVE"
(config-if)#ip address "172.16.0.x/30"
(config-if)#no shutdown
Creating the vPC domain and configuring the keep-alive link. This actually tells vPC to use the VRF we created for the keep alive instance and the end points. This will need to be done on both switches with the source and destination swapped.
(config)#vpc domain "100"
(config-vpc-domain)# peer-keepalive destination "172.16.0.x" source "172.16.0.x" vrf "VPC_KEEPALIVE"
We will now configure the vPC peer-gateway command on the vPC domain (this will be talked about later on in the HSRP section and is the recommended config).
(config-vpc-domain)# peer-gateway
The vPC keepalive is now configured.
Now we create the peer-link interfaces that traffic will actually travel on between the peers.
(config)#int "e1/1-2"
(config-if-range)#channel-group "1" mode "active"
(config-if-range)#no shut
We configure it as a trunk with the port type and say it is a vpc peer-link.
We will want to allow all vlans on the peer-link and not have it pruned.
(config)#int "port-channel 1"
(config-if)# switchport mode trunk
(config-if)# spanning-tree port type network
(config-if)# switchport "trunk" native vlan "20"
(config-if)# switchport "trunk" allowed vlan "all"
(config-if)# vpc peer-link
Configuring the vPC peers is now complete.
The next and final steps involve the interfaces that go to whatever access layer device you are using along with the device interfaces back from that device.
The channel-group does not need to be the same for both switches on the member link as this is local. However, it is good practice to do so for documentation and troubleshooting purposes.
You will want to do this for each link to the access layer, they may or may not need different allowed vlan configs.
(config)#int "e1/4"
(config-if-range)#channel-group "2" mode "active"
(config-if-range)#no shut
(config)#int "port-channel 2"
(config-if)# switchport mode trunk
(config-if)# switchport "trunk" allowed vlan "10,11,20"
(config-if)# vpc 2
Interfaces to vPC peers from the access device. This may be different depending on device used.
SW_1
(config)#int range "g0/0-1"
(config-if-range)#channel-group "1" mode "active"
(config-if-range)#no shut
(config)#int "port-channel 1"
(config-if)# switchport "trunk" "encapsulation" "dot1q"
(config-if)# switchport mode trunk
(config-if)# switchport "trunk" allowed vlan "##"
(config-if)# switchport "trunk" native vlan "##"
The access ports will need to be configured next.
(config)# int "g0/2"
(config-if)# switchport mode "active"
(config-if)# switchport access vlan "##"
(config-if)# switchport mode "access"
Vlan Configurations
To add a vlan to an existing link use the add command or it will override.
(config-if)# switchport "trunk" allowed vlan add "11"
You will want to make sure the vlans are created on each switch (including SW_1) as well.
(config)#vlan "10"
NOTE: Vlan differences are not reasons for the vPC peers to be down; they will be active but not have active vlans if incorrectly configured.
VRF-VLAN Binding (optional)
Binding the vPC VRF and VLAN is required to allow non-VPC VLANS and receivers to get multicast traffic. These are NOT trunked over the peer-link.
(config)#vpc bind-vrf "VPC_KEEPALIVE vlan "##"
HSRP and Vlan Interfaces
When using HSRP with vPCs both sessions will be in active/active mode.
This allows both devices to forward as intended in a vPC setup.
When using vPC in this configuration we will want to use the vPC command "peer-gateway". This command allows both peers to accept packets designated to the MAC address of the other peer.
We will configure the vlan interface. This will be the default-gateway of devices on the vlan with the HSRP virtual IP being the actual default-gateway address.
This will need to be configured for each vlan on each nexus device. You do not need to have the primary HSRP device be the same. However, they both will accept since we have the "peer-gateway" command configured.
(config)#int "vlan" "10"
(config-if)# no shut
(config-if)# ip address "172.168.10.x/24"
(config-if)# hsrp version 2
(config-if-hsrp)# hsrp "10"
(config-if-hsrp)# name VLAN10
(config-if-hsrp)# ip "172.168.10.254"
(config-if-hsrp)# priority 105
Access port VPC
Using vPC with an access port directly with a device such as a server is similar to the setup above, but it does not use a trunk port. This is not supported on all devices and will vary by make/model.
Misc Commands
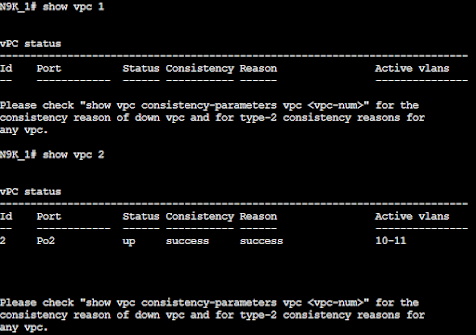
N9K_1# show vpc
When showing vPCs the id for the keep-alive does not show when doing show vpc "id" like below. Only our peer-link shows up.
N9K_1# show vpc "2"
N9K_1# show vpc statistics peer-link
N9K_1# show vpc statistics peer-keepalive
N9K_1# show vpc role